Iranian Hackers Expected to React to U.S. Exit of Nuclear DealIranian Hackers Expected to React to U.S. Exit of Nuclear Deal
The 2010 Stuxnet attack against Iran has become a prime example of an IoT attack. Now that the U.S. has exited the Iranian nuclear deal, retaliation is likely.
May 9, 2018

How might Iran respond to the U.S. pulling out of the nuclear deal? The nation is unlikely to shrug it off, as the country finds itself confronting a perilous economy, severe drought, heightened intra-regional tensions and the prospect of renewed sanctions, even as European partners that signed the agreement remain committed to it. “We are not going to permit Trump to win this psychological war,” Iran’s President Hassan Rouhani recently said. Iran’s supreme leader Ayatollah Ali Khamenei, who is the highest ranking political and religious leader in the country, recently called Muslim nations to “stand united against America and other enemies.”
Iran tends to respond to confrontation through clandestine cyber measures. This fact has been the case since 2010, after the United States and Israel reportedly unleashed the Stuxnet worm on the nation with the intent of decimating its nuclear enrichment capabilities. The attack reportedly succeeded in destroying roughly 1,000 of Iran’s nuclear centrifuges, and, in the process, became an archetypal example of the power of IIoT-based cyberattacks. But in the aftermath of Stuxnet, the country responded by investing more resources in its nuclear program while also building up its own cyber army, as well as supporting Iranian hackers’ efforts to attack U.S. targets. Before the nuclear deal was signed, the country engaged in one of the most substantial series of attacks to be perpetrated against the United States, hitting the financial sector, government agencies, universities, among other targets. A document leaked by Edward Snowden indicates that Iranian hackers learn from U.S. cyber initiatives and, earlier this year, Wired magazine wrote that Iranian hackers had been using the EternalBlue cyberweapon, purportedly developed by NSA.
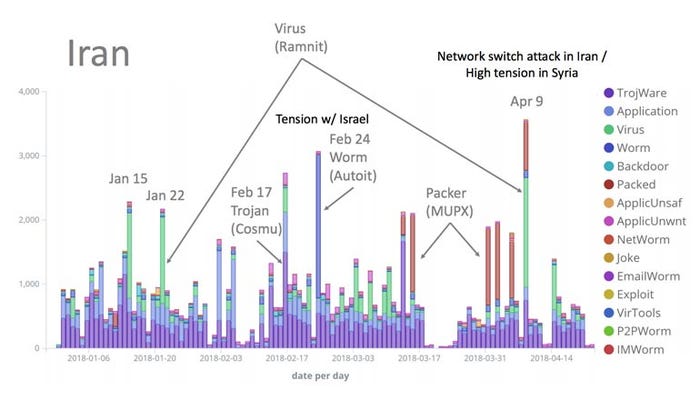
Comodo had noticed an uptick of cyberattacks on Iran in the first quarter of 2018.
“I can only estimate that there will be some cyber retaliation [following the U.S. exit of the nuclear deal],” said Yotam Gutman, vice president of marketing at SecuriThings. Conflicts between Iran and the United States have de-escalated in the wake of the 2015 nuclear deal; it stands to reason that such attacks could ramp up following the U.S. exit of the agreement. If history is a guide, Iran could provide support to individual hackers to launch attacks on U.S. targets such as critical infrastructure, government agencies, universities and financial institutions. Even though Iran has a substantial cyber army, it often assigns hacking jobs to other state-sponsored entities. “That seems to be their preferred method of operations,” Gutman said. “It is also likely they will attack semi-important targets, as they have done before,” he added, citing Operation Ababil, a long-standing series of attacks that the Washington Post reported that had the support of the Iranian government.
[Internet of Things World addresses the security concerns for IoT implementation in every vertical, attracting senior security professionals from the world’s biggest organizations. Get your tickets and free expo passes now.]
Iran, itself, has seen an uptick in cyberattacks in recent months as tensions mount between the nation and Israel, according to malware research firm Comodo. The two nations are engaged in a proxy war in Syria, with Israel bombing Iranian military sites in Syria. Saudi Arabia finds itself in a similar position vis-à-vis Iran.
But cyberconflicts involving Iran are nothing new. For the past four decades, Iran has found itself facing a cold war with the United States, which has progressively moved into cyberspace, and, in recent years, into the IoT domain. For instance, in 2016, The New York Times wrote that Iran targeted the Bowman Avenue Dam north of Long Island. While Iranian hackers are typically adept at masking their identities, making attribution tricky, a report from the Carnegie Endowment for International Peace states many of the nations’ cyberattacks can be traced to its Ministry of Intelligence and Islamic Revolutionary Guard Corps. Security researchers at CyberX have theorized that the industrial malware known Triton and Trisis was likely authored by Iranian threat actors.
The nation’s cyber efforts have grown significantly more sophisticated in recent months. “There’s definitely a lot of fear by the intelligence agencies and lots of security companies about what Iran is going to do,” Charles Carmakal, vice president at Mandiant told The Hill in March. Evidence is also building that Iranian hackers are targeting the military, aviation and energy sectors, all of which are increasingly deploying Internet of Things technologies.
About the Author
You May Also Like






