How the Mirai Botnet Could Make Mobsters Out of Hackers
The rules of cybersecurity have changed after hackers shut down half the Internet last Friday with a massive IoT-fueled attack.
October 25, 2016

Earlier this month, President Obama lamented that the Internet is like the Wild West. Russian hackers are meddling in the U.S. election, and no one seems able to stop them or other determined cybercriminals. But with the IoT-fueled Mirai botnet that brought down half the Internet on Friday, the Internet could become like Sicily under mob rule.
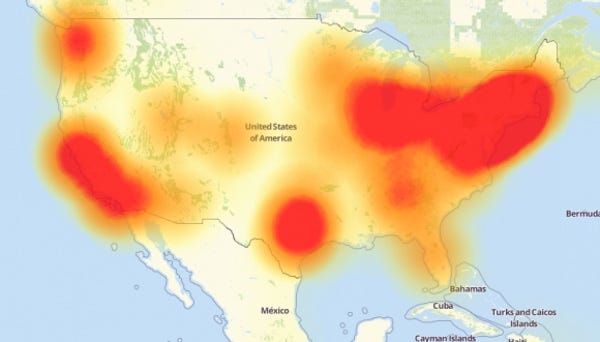
Last Friday’s attack flooded Internet performance company Dyn’s servers, peaking at one terabit per second per second. The hack caused the biggest Internet outage yet, preventing millions of people across the U.S. from accessing sites like Amazon, PayPal, Twitter, Spotify, Netflix, AirBnB, and CNN.
“With Mirai, a hacker could say: ‘hey, we took you offline. We are going to keep you offline until you start paying. That is basically just like the Mafia,” says security expert Pablos Holman, who is the keynote speaker at next week’s IoT Emerge in Chicago. “You pay us for protection and if you don’t pay, guess what, I have a cousin who is in the DDoS business.’”
Chase Cunningham, Ph.D., A10 Networks’ director of cyber operations, also agrees that such extortion hijacks are possible. Since the code for Mirai is freely available online, it is relatively simple to launch.
Already, the people launching DDoS attacks are taking a page out of the Mafia handbook in that they aggressively target anyone who they fear could reveal them. After security expert Brian Krebs wrote about an Israeli online DDoS service, his website was hit with a crippling DDoS hijack. And shortly after a Dyn researcher Doug Madory gave a talk on the subject at Nanog (video below), Dyn was hit with its own massive attack:
The person who wrote the code advertises that fact, declaring in the notes released alongside the code: “All scripts and everything are included to set up working botnet in under 1 hours. I am willing to help if you have individual questions […].”
The author of Mirai also claims to have profited from DDoS attacks, stating: “When I first go in DDoS industry, I wasn't planning on staying in it long. I made my money, there's lots of eyes looking at IOT now, so it's time to GTFO.”
Thomas Pore, director of IT and services at Plixer, also predicts that cybercriminals could begin using Mirai and other DDoS hijacks to extort their victims. “If they have the botnet up and running, they don’t need to break into anything. They just need to take out the legs that hold everything up. Clearly, the attack on Friday showed that you can take out a huge resource and it is going to affect a lot of people.”
The threat of ransomware, which locks computers until a sum or money is paid, has been growing exponentially in recent years. Mirai technology could give cybercriminals a new tool to conduct hijacks for ransom on a bigger scale.
Some hackers were already threatening to deploy botnets as extortion before Mirai hit.
And evidence exists that hackers have made money off of similar hijacks. A DDoS database known as vDOS apparently raked in $600,000 in two years, according to Brian Krebs, whose blog was the victim of the first large Mirai attack.
In addition, ads are popping up on underground websites promising to rent access to one of the largest IoT botnets in the world. For just $7,500, anyone can have access to 100,000 IoT bots, according to the ad discovered by Forbes. The seller claims the bots can drive one terabit of data per second of traffic, which amounts to 128 gigabytes.
Future DDoS hacks could be more than a nuisance. Cybercriminals could launch targeted DDoS hijacks that threaten freedom of speech. It is relatively simple for a DDoS attack to bring down a website hosting editorial content. Or hackers could attack a hospital’s Internet connection and demand payment before they switch it back on. They could do the same thing with 911 services. Late last month, researchers at Cyber-Security Research Center in Israel reported that exploiting about 6000 smartphones would be enough to cripple 911 in a U.S. state. Targeting 200,000 smartphones could theoretically cripple the nation's 911 service, they say.
In any event, Mirai and other types of DDoS attacks give the lone hackers toiling away in a basement somewhere enormous power to launch attacks that cause financial damage. Brian Krebs estimated that it will cost a DNS service provider between $100,000 and $300,000 per year to protect itself from similar hicacks to the one he faced in September. The company Akamai Technologies, the content delivery network that that hosted Krebs’ blog, broke ties with him after that attack. Tom Leighton, co-founder and CEO of Akamai, explained the break with Krebs, telling the Boston Globe that such attacks, if sustained, could cost the company millions of dollars each year to battle.
For now, Google has offered to host the krebsonsecurity.com site under its Project Shield, which was designed to protect news, human rights, and elections monitoring sites. But less fortunate websites could go dark when facing DDoS-driven traffic surges.
Developers of IoT devices will likely face growing scrutiny from their customers about security. In the aftermath of Friday's hack, the Chinese electronic firm Hangzhou XiongMai, whose webcams were used in the Mirai breach, has already announced a plan to recall some of its connected devices.
“I am hoping it is a wake-up call, but I am sure it will be like most other things in security where people freak out about it and then move onto the next issue. I am sure we will see more of these attacks in the near future,” says Chase Cunningham, Ph.D., who is A10 Networks’ director of cyber operations. “I am interested to see what happens with the election coming up. I think we are probably due to see some big DDoS events specific to the election.” Given the alarming number of cybersecurity breaches in 2016, Cunningham may be proven correct.
About the Author
You May Also Like






