A New Version of the Mirai Botnet EmergesA New Version of the Mirai Botnet Emerges
The infamous IoT botnet continues to evolve.
March 30, 2017

The story behind the Mirai botnet is so abstract, you might think it was devised by an imaginative novelist. To cite but two of the story elements: First, there’s the notion of DVRs and video cameras playing a role in knocking prominent sites ranging from Amazon to Reddit off the internet. And then there is this wrinkle: The purported mastermind behind Mirai, Paras Jha, runs a DDoS protection service known as ProTraf Solutions, according to security researcher Brian Krebs.
The latest wrinkle is that a new variant of Mirai attacked an unnamed U.S. college for 54 hours straight, starting on February 28. “The average traffic flow came in at over 30,000 RPS and peaked at around 37,000 RPS—the most we’ve seen out of any Mirai botnet. In total, the attack generated over 2.8 billion requests,” writes Dima Bekerman, a security researcher at Imperva Incapsula in a blog post.
It was a bad omen when the source code for the Mirai botnet turned up on the Hack Forums website, giving cybercriminals across the world a new tool to modify for custom attacks. (Going by the name “Anna Senpai,” the person who posted the code used the above picture as an avatar.) After taking down Spotify, Reddit, Twitter, and Amazon in October 2016, Mirai took down attacked routers from Zyxel and Speedport—disrupting internet service for nearly one million Deutsche Telekom customers a month later. And in December, a new version of Mirai popped up infecting TalkTalk Telecom home routers.
In 2017, the Mirai code has continued to fork and evolve into new variants. A new strain popped up targeting Linux machines.
But one point of interest about the late-February attack against a U.S. college is its focus on the application layer for the assault. To date, Mirai has predominantly focused on network-layer DDoS exploits.
Imperva Incapsula researchers caught wind of the malware by analyzing factors such as header order, header values, and types of devices. “Our research showed that the pool of attacking devices included those commonly used by Mirai, including CCTV cameras, DVRs, and routers,” writes Bekerman of Imperva Incapsula. “We also noticed that the DDoS bots used in the attack were hiding behind different user-agents than the five hardcoded in the default Mirai version. This–and the size of the attack itself–led us to believe that we might be dealing with a new variant, which was modified to launch more elaborate application layer attacks.”
In the end, Bekerman says that the 54-hour duration of the attack is remarkable. “[W]ith over 90 percent of all application layer assaults lasting under six hours, an attack of this duration stands in a league of its own,” he concludes.
When asked about the potential intent behind the most-recent attack, Igal Zeifman, senior manager at Imperva says: “It's hard to say and I wouldn't want to speculate. One thing to note here is that we didn't get information from the customer about any ransom threats or similar, so we can rule that motive/bad actor type out.”
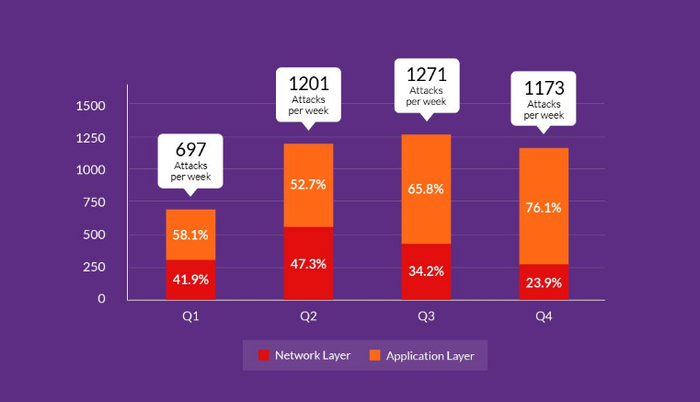
Zeifman concludes: “We say that this variant of Mirai might be a symptom of the increased application layer DDoS attack activity we saw in the second half of 2016. I definitely noticed an uptrend in the sheer numbers of application attacks during 2016 (see images below, from our EOY infographic), which will likely continue in 2017. That said, over 90 percent of attacks we mitigated in the last quarter of 2016 lasted under six hours. This attack, that went on for a 54 hours straight is in a league of its own.”
About the Author
You May Also Like






