Securing our smart homesSecuring our smart homes
August 24, 2021

Sponsored Content
By Patrick Carrier, Business Development, Connected Secure Systems, Infineon
Our homes are becoming smarter as both individual appliances and larger domestic infrastructure gain connectivity and processing power. These systems are being connected to each other and to the internet, as well as being integrated with voice interfaces such as Amazon’s Alexa, Apple’s Siri, and Hey Google, to create sophisticated home-automation schemes. Who would have thought, ten years ago, that it would be possible to say “Movie night” and have your home’s doors and windows locked, curtains drawn, lights dimmed, room temperature set and TV turned on? But this is very achievable today.
Smart-home technology promises many other ways to make our home lives easier and more convenient, from programmable lighting schedules to automated garage doors. What is less remarked upon is the work that is needed to enable this convenience while ensuring that smart homes keep residents and their data secure. As we are beginning to realize, more that 15 years after we started carrying smartphones, our online data footprint is incredibly revealing of our lives and actions, desires and failings. Data gathered from within our homes will be even more revealing. If our homes are our sanctuaries, poorly secured smart-home technology threatens, metaphorically at least, to tear down the curtains, fit floor-to-ceiling windows, and build a viewing gallery for curious passers-by.
Given the potential value of data about activities within our homes, there are plenty of incentives to abuse smart-home technology for gain. One of the simplest approaches to doing so is for legitimate smart-home technology to over-gather and over-share information about the way it is used: anyone who has monitored the network connections that a smart TV makes when connected to the Internet will be familiar with this approach to appropriating personal data for commercial gain. Another mass-scale approach is to trawl the Internet for badly secured Internet of Things (IoT) devices, and then co-opt them into botnets that can be used to launch denial-of-service attacks for political or financial gain.
Perhaps the most disturbing type of hack, though, is one that exploits smart-home technology to attack an individual. In December 2020, America’s Federal Bureau of Investigation warned that hackers are now using compromised smart home devices to orchestrate ‘swatting’ attacks. The hackers use stolen credentials to log in to a victim’s livestreaming camera and/or smart speaker. They then call the emergency services to report that a crime is underway at the home. Once the responding police arrive, the hackers watch the action through the camera and interact with the police through the speaker. In some cases, hackers stream the attack online.
The challenge of securing the smart home
As smart-home technology becomes more complex and widely deployed, the challenge of securing it increases.
One of the most fundamental parts of IoT security, of which the smart home is a special case, is device authentication – in other words, finding a way to prove that each device on a network is legitimate and has not been cloned. This means giving each device a unique identifier, ideally held in hardware, which cannot be altered or copied. The unique identifier can then be used as the basis of a series of steps that establish trust between two devices, by enabling the verification of their identities. Once this is done, it’s possible to establish a secret that is shared by the two devices, which is then used to enable secure communications between them.
Another key aspect of securing smart-home devices involves ensuring that any firmware downloads they receive are legitimate. This involves two steps. The first is to ensure that any source of firmware updates signs the code it sends, so that the smart device can check that it has come from a legitimate source. The second step is to give the smart device a way to check that the code hasn’t been altered in transit. If the signature is not recognized as a valid source or the payload appears to have changed in transit, then the update should be rejected.
This is obviously important from a practical device security point of view but is also becoming a requirement of emerging IoT standards, accreditation schemes and regulations. If a vendor can’t show that it can update a device’s firmware securely in the field, the equipment may be locked out of some markets. Some regulators even want equipment providers to provide a ‘best before’ date at point of sale, so that buyers will know for how long they can expect vendors to maintain their devices’ security. This would demand a greater commitment from device makers in the smart-home market than those selling general consumer electronics.
Secure communication, using encryption schemes that reference a device’s unique ID, is also very important to protect data integrity and user privacy in smart-home set-ups. For example, sound that has been captured by a voice assistant must be encrypted to secure its journey to the cloud servers that provide voice-recognition services. Video data streamed from nanny cams must be encrypted to ensure privacy. Other devices that gather and transmit data, such as thermostats and air-quality monitors, also need to be securely authenticated, and use encryption to protect the integrity of the data they transmit so it cannot be corrupted or misused. Given that we use sensors to provide the information that automated systems use to make decisions about their actions, injecting false information into a sensor data stream could have serious consequences. For example, if someone manipulated your thermostat data to show warmer temperatures in your home than were actually present, this could cause your air conditioning (A/C) to run constantly. Worse, if they hacked thousands of thermostats in a city so that all the A/C units turned on at once, this could tax the power grid enough to cause a blackout.
A solution to securing the smart home
Security controller ICs such as the OPTIGATM Trust M from Infineon, are also known as embedded Secure Elements (eSEs). They have been designed to provide the means needed to secure smart-home devices and networks.
These ICs provide a layer of physical security by handling security functions in a separate device isolated from the main application processor of a smart-home device. Each has secure storage which can hold arbitrary user data and cryptographic keys either generated on the device or programmed into the device during its manufacturing in a secure facility. The devices are tamper-resistant, so trying to physically extract the secret information will destroy it. Some vendors, including Infineon, also run their own certificate authorities, so it is possible to authenticate each device as a genuine Infineon part.
Such eSEs can hold secret keys for use in symmetric cryptography schemes, they can create cryptographic key pairs for use in asymmetric cryptography schemes, and establish secure communications channels. The public keys of cryptographic key pairs can also be used to create a certificate, which can later be employed to verify the identity of a device.
eSEs can also be programmed with the credentials needed to automatically make secure connections to cloud servers, such as Amazon Web Services, at boot time.
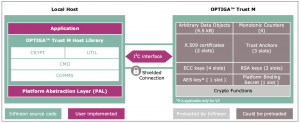
Figure 1 System Block Diagram
Successful security means paying attention to details – all of the details. For example, eSEs should protect their information exchange with a host application processor by using a secured communication channel. For another level of security, an eSE can be given a single-use key that it uses to carry out an exchange with the application processor to cryptographically ‘bind’ the two parts together when the system is started for the first time. This stops the security controller working with any other processor, even if the part is de-soldered from one board and used in another, protecting its secrets from misuse.
The eSE can create cryptographic key pairs, generate random numbers, calculate cryptographic hashes, and directly handle various forms of encryption and decryption. Some security controllers are also being designed with an eye on the future, supporting longer key lengths than are currently used so that they remain relevant as OEMs shift to more powerful cryptographic schemes.
Security controllers with this set of features provide a firm foundation on which to build a secure ‘chain of trust’ within smart-home devices and networks. Each security controller can be given a unique identifier, user secrets, and cryptographic keys. These are protected in hardware, so that every device can be authenticated and private information remains secret. Cryptographic keys and functions enable the establishment of secure communications channels, both across the Internet and within home networks, to protect data integrity and user privacy.
Smart homes can simplify our home lives by automating all sorts of basic functions within our homes. This promise of greater comfort and convenience must be tempered with concerns about the integrity of the devices and networks that enable it, and the privacy of the data about our lives that these systems capture. eSEs can provide many of the basic building blocks needed to establish and maintain the integrity and privacy of smart-home devices and systems.
Learn more at https://www.infineon.com/cms/en/about-infineon/make-iot-work/smart-home-and-building/ .
You May Also Like






