The 10 Most Vulnerable IoT Security TargetsThe 10 Most Vulnerable IoT Security Targets
From autos to video cameras, the Internet of Things is exponentially increasing the number of potential targets for cyber-criminals, as we explain in this article with an accompanying poll.
July 27, 2016

Already have an account?
Imagine the havoc that hackers could cause a nation by systematically targeting its power grid. Or the implications of criminals taking control over a city's network of video cameras. Or of a hacker taking control over a commercial airplane en route. While some of these risk scenarios may seem exaggerated, the ability of Stuxnet malware to cause physical damage has been shown in an Iranian nuclear facility. Last year, the Lloyds ‘Business Blackout' report stated that the U.S. power grid itself was at risk of a Stuxnet-style attack, potentially causing $1 trillion in damages.
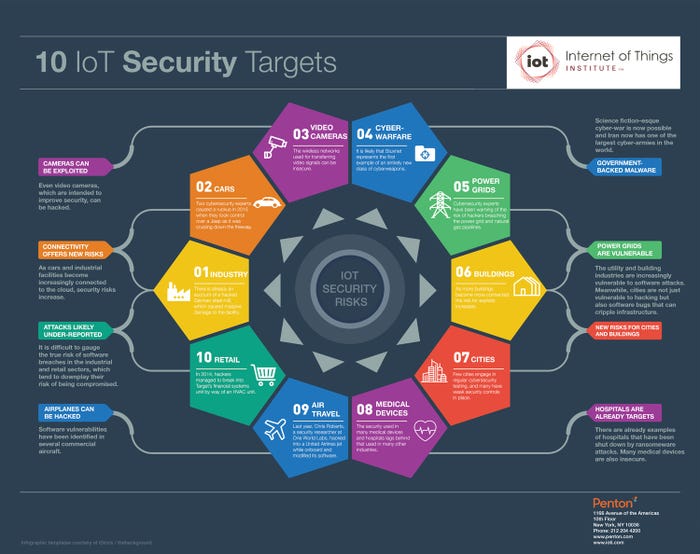
1. Industrial Facilities
There is already an account of a hacked German steel mill, which caused massive damage to the facility. Criminals used a combination of spear phishing and social engineering to gain access to the steel mill’s office network. From there, the hackers gained access to the production system and took over industrial control components in the plant.
It is difficult to know how off industrial plants are hacked for extortion because such breaches are rarely reported, according to Marina Krotofil of the Hamburg University of Technology.
At this stage in the game, we need to operate our networks as though a breach will occur.
Phishing and social engineering attacks are not going away anytime soon, says Thomas Pore, director of IT and services at Plixer. “Commercial facilities, along with every organization, need to provide training to users on how to identify phishing attacks or how to avoid being a victim of social engineering,” he says. “Users need to be trained not to click on links in emails. Training should not be a one-time event, at time of hire, it should be performed regularly, even quarterly. When a phishing attempt is identified, an announcement should be made to employees as an example of how to identify. Authentication and privilege should be configured under the principle of least privilege as well as implementing software restriction policies to help prevent an actor from gaining access to critical resources should a breach occur. At this stage in the game, we need to operate our networks as though a breach will occur.”
2. Cars
Two cybersecurity experts caused a ruckus in 2015 when they took control over a Jeep as it was cruising down the freeway. Although that was a stunt for Wired, the attack showed the potential for how dangerous such attacks could be in theory and led to its recall of 1.4 million vehicles. Fiat Chrysler recently indicated it had a new strategy for addressing security holes—pay security experts to find them. The company has a bug bounty program to reward experts anywhere from $150 to $1500 each time they find a security weakness and share it with the company.
Perhaps it goes without saying that the most dangerous part of the connected car is the ‘connected’ part.
Recent evidence suggests that some high-tech thieves are now using laptops to steal cars. But the threats become much greater as cars become ever-more connected, not to mention semi- and fully-autonomous.
“Perhaps it goes without saying that the most dangerous part of the connected car is the ‘connected’ part,” says Cesare Garlati, chief security strategist at prpl Foundation. “We’ve seen recently with the Nissan Leaf that researcher Troy Hunt was able to drain the car of its battery life using little more than its vehicle identification number (VIN) and accessing the car’s climate control system. While this, strictly speaking, isn’t life threatening, it’s a good example of how – using a little lateral thinking – one part of the car’s anatomy can be used to get to another.” Garlati says this could have dangerous consequences if hackers found their way into more critical functions, such as the steering and brakes as researchers were able to do with a Jeep back in 2014.
[Related: What IT Pros Can Learn From the Top 5 Data Hacks]
“The situation is made worse because many engineers tasked with designing and building systems are not experts in network protocols and even less versed in network security,” Garlati says. “They may know how to put together hardware components, but implementing TCP/IP protocols is a rarefied discipline which requires expert knowledge and extensive debug and testing. While it’s unfair to expect mechanical and electrical engineers to shoulder this burden, the lack of subject matter expertise is leaving systems wide open to attack, something which vendors, regulators and manufacturers must carefully consider as the evolution of connected cars continues.”
“The future of connected-cars has the potential of being very dangerous,” agrees Thomas Pore, director of IT and services at Plixer. “There is no such thing as infallible code, meaning that a product while completely secure today could be exploited tomorrow. Bug bounty programs have been around for a while but have increased in popularity, recently. This is great in concept and will prove useful as weaknesses will be discovered however this does not remove all the risk. Ethical security experts will reap the rewards, but what about the unethical actors out there that could care less about $1500, but will hold out for the highest bidder. Zero-day vulnerbilities around autonomous features could be exploited to create giant traffic jams or even in assassination attempts.”
3. Video Cameras
Surveillance cameras are intended to make us more secure, and many cities across the U.S. have installed them, thanks to grants from the Department of Homeland Security. But the wireless networks used for transferring video signals can be insecure. In 2014, two security experts announced at Defcon that they managed to break into a police wireless mesh network in an unnamed town. “We could do all sorts of tomfoolery — hey, let’s have Godzilla walk down the street,” said Dustin Hoffman, the president of Exigent Systems to VentureBeat. “Or we could do the opposite and send police resources elsewhere.”
Another risk with video cameras—and other IoT devices—is the ability for them to be used to create botnets to send spam and ransomware, launch DDoS attacks, and commit other mischief.
“Another risk with video cameras—and other IoT devices—is the ability for them to be used to create botnets to send spam and ransomware, launch DDoS attacks, and commit other mischief,” Cesare Garlati, chief security strategist at prpl Foundation says. “The very fact that patching isn't high on the priority list for admins is testament to why security in devices like CCTV cameras needs to be ‘baked in' at the chip or hardware layer. If we don't take steps now to improve security within devices at the development level, the results could be catastrophic, especially when they can be hijacked and directed at critical infrastructure.”
“Cameras will always be a target of hackers as they can potentially provide sensitive video or even audio into a target network,” says Thomas Pore, director of IT and services at Plixer. “Additionally, a compromised camera can be used to a critical foothold into a target network as well as be used to alter audio/visual settings that would interfere with monitoring. They are often easy targets as many deploy cameras with public facing IPs, allowing anyone to send/receive packets from it. Also, camera firmware is often not maintained for great length as development of newer technologies becomes a priority, and even if firmware does get patched, many cameras will never see an update. In the case of 2 experts hacking into a wireless mesh network, it was identified that this was largely based on implementation failure from the vendor. Perhaps this could have been avoided by betting managing/monitoring risk during vendor selection.”
4. IoT-Enabled Spying and Potential for Cyberwarfare
“Science fiction cyber-war is here,” according to Oscar-winning filmmaker Alex Gibney whose recent Zero Days flick examines that Stuxnet worm that was far more advanced than ordinary malware. Purportedly developed by the U.S. and Israel, the Stuxnet worm proved that it is now possible for a worm to attack critical infrastructure. The worm was first detected about six years ago and is reported to have ruined of fifth of Iran’s nuclear centrifuges.
Stuxnet can target programmable logic controllers (PLCs) and supervisory control and data acquisition (SCADA) systems, enabling it to target a vast number of systems.
According to the film Zero Days, it is likely that Stuxnet represents the first example of an entirely new class of cyberweapons. After Iran discovered the worm, the nation would go on expand their nuclear program and create one of the largest cyber-armies in the world. In 2012, Iran would go onto attack Saudi Aramco, the biggest oil company in the world. Earlier this year, 7 Iranians were charged with launching computer attacks targeting American banks and a dam in New York.
In a Black Hat 2015 presentation, researchers Runa Sandvik and Michael Auger claimed to have found a way to hack the ShotView targeting system on Tracking Point’s hi-tech Linux-powered rifles.
The United States purportedly developed and shelved a plan known as Nitro Zeus designed to bring down Iran’s air defenses, communications equipment, and much of its electrical grid.
On a related note, the Internet of Things could provide new avenues for spying. NSA deputy director Richard Ledgett admitted as much earlier this year, stating that the agency was looking into spying on the Internet of Things.
“In a Black Hat 2015 presentation, researchers Runa Sandvik and Michael Auger claimed to have found a way to hack the ShotView targeting system on Tracking Point’s hi-tech Linux-powered rifles,” explains Cesare Garlati, chief security strategist at prpl Foundation. “The company’s .338 TP bolt-action sniper rifle is said to provide precise impact on targets out to .75 mile. Although they claimed the company had ‘done a lot right’ and minimized the attack surface, the researchers were still able to compromise the rifle via its Wi-Fi connection, exploiting software vulnerabilities to prevent the gun from firing, or even to cause it to hit another target according to their instructions.”
Fortunately, a remote attack on the rifle couldn’t make it fire as that requires a physical pull on the trigger, Garlati adds. “However, Sandvik and Auger were able to demonstrate how to effectively brick the rifle, making its computer-based targeting permanently unusable. For a weapon that costs $13,000 and could be highly dangerous in the wrong hands, the research is concerning.”
5. Power Grids and Utilities
In January, Ukraine accused Russian hackers of shutting down almost a quarter of its power infrastructure, knocking out at least 30 of its 135 power substations. While matching that feat in the United States may be slightly more complicated, it is not apparently very difficult at some facilities here. In April, a team of white-hat hackers known as RedTeam showed how easy it was to break into a U.S. power company’s grid in a matter of days.
In addition, cybersecurity experts have been warning of the risk of hackers breaching the power grid and natural gas pipelines. The fact that squirrels and other rodents cause some 200 power outages per year raises the question of what determined cyber-attackers could do. Imagine the impact of wiping out power of, say, most of the East Coast for even 24 hours. It is not only an abstract risk. In 2013, the Metcalf sniper attack of a California energy grid caused $15 million in damages.
Imagine the damage someone could do simply tossing a bomb over the fence or driving a car bomb into the center of the sub station.
“Yes, squirrels or other rodents can take out power due to their physical access,” Pore says. “The electrical substation that services my house is a few miles down the road and supplies power to an entire town. It also happens to be located just off the road (~50 ft) guarded by nothing more than a chain link fence. Imagine the damage someone could do simply tossing a bomb over the fence or driving a car bomb into the center of the sub station,” Pore adds. “One could do some very serious damage quickly since it is unguarded,” Pore explains. “Since networks of power grids and utilities are classified as a critical sector, their should be continuous audits and penetration testing performed, similar to RedTeam breaking a power grid. Simply following a framework, such as NIST, is not enough anymore. The bad guys are reading the same material and to maintain operation excellence, additional security strategies and analytic modeling using network traffic coupled with contextual detail, user/badge authentications, will need to be implemented.”
The Stuxnet worm, which was already mentioned here, was reportedly developed to bring down Iran’s nuclear power plants suspected of enriching uranium.
“The attack on Ukraine’s power grid was a very frightening example!” says Cesare Garlati, chief security strategist at prpl Foundation. “At its core, it involved connected devices used in industrial control and automation (IoT): attackers wrote malicious firmware to replace the legitimate firmware on serial-to-Ethernet converters at more than a dozen substations (the converters are used to process commands sent from the SCADA network to the substation control systems). Taking out the converters prevented operators from sending remote commands to re-open breakers once a blackout occurred.”
“While targeted attacks such as Stuxnet and Nitro Zeus are carefully articulated to gain entry into secure facilities, the world of IoT creates significantly more opportunities to get a foothold into a network. It is not surprising that the NSA is excited to see the market grow quickly,” Pore says. “In an effort for companies to get products to market first, product security takes a back seat to product design. IoT is supposed to make life more convenient, however convenience compromises security.”
6. Buildings
The building industry has been slower than many to embrace digital technology. But that is beginning to change quickly as building automation technology rapidly gains in popularity. As more buildings become connected, the risk for exploits increases. Already in 2013, Google saw its Wharf 7 office in Sydney, Australia get hacked by way of its building management system. One of the hackers, Billy Rios, told BBC that the building systems were very simple to breach. Rios estimates that there are some 50,000 globally that are connected. Of those, 2000 are online and don’t have any password protection, inviting criminals to access their heating and cooling systems and potentially take control over their connected door locks.
When it comes to IoT in the home, people must realize that security of these devices just doesn’t exist yet.
“The home is something that is precious – you wouldn’t just allow anyone through your front door, so why do people do it with their connected devices so willingly?” Garlati asks. “When it comes to IoT in the home, people must realize that security of these devices just doesn’t exist yet.”
“A case such as the exposure of vulnerabilities in Samsung’s SmartHome platform bring forward a number of questions, particularly: Do these systems really need a mobile app? Does the app really need to connect to central server in the cloud? And most importantly, is it sound to have a smartphone (especially running on Android) control anything that is critical to you?” Garlati says.
“These are all key questions to address when we look at IoT especially in the home as a vast majority will not use apps that are developed by the OEM, but rather assembled using a host of third parties – of which they have no control or visibility over,” Garlati notes. “To combat this, OEMs should implement open and interoperable standards in their devices and Home IoT Architecture should rely only on a local hub, and this hub should be secured. If researchers can break these devices, it’s a safe bet that criminals may have already found a way in, too.”
“You can do all the vulnerability patching you want, but if the basic security strategy of authentication for privilege is not being configured, it’s time to reevaluate the vendor,” Thomas Pore says. “Developing guidelines on how tech will be deployed and auditing the deployment based on the guidelines will help reduce third party risk.”
7. City Infrastructure and Transportation Networks
Last year, Cesar Cerrudo, CTO of IOActive Labs proclaimed that many cities risk cyberattacks—even those who don’t consider themselves to be so-called “smart cities.” The majority of cities around the world use at least some form of connected technology to manage everything from traffic to lighting to public transit. Still, few cities engage in regular cybersecurity testing, and many have weak security controls in place.
But it doesn't take a full-fledged cyberattack to cause problems. Even software bugs can cause significant glitches. For instance, Lake Tahoe–adjacent Placer County accidentally summoned 12,000 of its citizens to jury duty on one morning in May 2012, snarling traffic in the air. And on November 22, 2013, the San Francisco Bay Area Rapid Transit (BART) system was brought to its news as a result of a software glitch, trapping a total of 500 to 1000 passengers onboard.
“We’ve also seen that Transport for London is looking to IoT sensors and the data they provide to help improve congestion for commuters, but they must not overlook wider security and privacy implications this will have on the City of London,” Garlati explains. “IoT, although growing at an enormous pace, is still very much in its infancy – with people eager to get their hands on the latest and greatest connected devices and manufacturers rushing to get them to market – security is often an afterthought.”
At worst, poor security controls will mean terrorists will have access to a whole host of information they can use for surveillance or other nefarious purposes
If IoT developers don’t take steps now to improve security within devices at the development level, the results could be catastrophic, especially when used to capture data on passengers and whole cities as suggested by TfL’s CIO, Steve Townsend. “At best, people’s privacy and civil liberties are affected. At worst, poor security controls will mean terrorists will have access to a whole host of information they can use for surveillance or other nefarious purposes when security controls aren’t properly addressed,” Garlati says.
For this reason the prpl Foundation has provided guidance on how to create a more secure Internet of Things that advises manufacturers and developers to adopt a hardware-led approach that sees security embedded from the ground up.
8. Medical Devices and Hospitals
The security used in many medical devices and hospitals lags behind that used in many other industries. Not long ago, it was a common occurrence for some medical devices to have hard-coded passwords. Within hospitals, tales abound of staff that have Post-It notes with passwords scribbled on them. Already, several hospitals have been hit with ransomware including Hollywood Presbyterian Medical Center in Los Angeles, which was attacked earlier this year. Attackers brought down computers for a week using ransomware and ultimately extorted $17,000 from hospital administrators.
The notion of terrorists hacking the vice president’s pacemaker was made famous in the show Homeland. While it is theoretically possible for hackers to maim or kill patients that use medical devices, perhaps a bigger threat relates to data breaches. Medical devices that are connected to databases with sensitive patient information that can be used for identity theft.
Hackers could breach IoT-enabled hearing aids to snoop on people at home and at work.
“Healthcare is another industry that is coming to rely on connected devices and smart sensors to help medical professionals provide more effective patient care,” Garlati explains. “However, the US Food and Drug Administration (FDA) was forced to warn hospitals in 2015 against using a popular internet-connected drug infusion pump after research from Billy Rios revealed it could be remotely hacked. Attacks like this may be harmful to human lives as medicine applied in wrong dosages becomes a potentially lethal weapon.
It had the following warning: “This could allow an unauthorized user to control the device and change the dosage the pump delivers, which could lead to over- or under-infusion of critical patient therapies.”
The affected devices were the Hospira Symbiq Infusion System (v3.13 and earlier), the Plum A+ Infusion System (v13.4 and earlier), and the Plum A+ 3 Infusion System (v13.6 and earlier). “The manufacturer has claimed there are no known cases where these pumps have been accessed remotely by unauthorized parties. It is also claiming that most of these devices will be replaced in the next 2–3 years,” Garlati explains. “However, with the healthcare IoT market set to be worth $117 billion by 2020, according to MarketResearch.com, there’s an increasing need for manufacturers to reengineer vital systems to ensure they can’t be misused in this way.”
Medical Personally identifiable information (PII) sells for 10–20 times the price of a U.S. credit card number on the dark web.
“Medical Personally identifiable information (PII) is worth considerably more than other types of PII and sells for 10–20 times the price of a U.S. credit card number on the dark web,” Pore says. “The risk around compromising medical devices within hospitals, even ransomware, is geared around the real-time assistance the hospital provides. Hospitals cannot afford to have their servers locked down with ransomware and restoring from a backup takes time, which many do not have. The risk of physical harm around compromising medical records lays around the concept of a mixed medical record where someone receives care in the name of someone else. The fraudulent user’s medical information becomes mixed in with the true patient’s information which could have severe consequences, such as the prescriptions of medications. Routine off-site or off-network backups of critical systems is the only sure-fire way to recover from ransomware. User training to identify phishing attacks is also paramount. User just love clicking on URLs in email. The FBI is taking a firm stance on not paying ransoms, however each case is different.”
9. Airplanes
Last year, Chris Roberts, a security researcher at One World Labs, made headlines after boasting that he hacked into a United Airlines jet and modified code on the craft’s thrust management computer while onboard. An FBI search warrant states that he succeeded in commanding the plane to climb, altering the plane’s course. Roberts told the FBI that he had identified vulnerabilities in several commercial aircraft, including the Boeing 737-800, 737-900, 757-200, and the Airbus A-320. Roberts boasted that, in 2012, he had hacked into the International Space Station.
Chris Roberts was apparently able to overwrite code on the airplane’s Thrust Management Computer while aboard a flight, causing a plane to move laterally in the air.
Airplanes today are controlled by complex connected computer systems. “Sensors all over the aircraft monitor key performance parameters for maintenance and flight safety,” Garlati explains. “On-board computers control everything from navigation to in-cabin temperature and entertainment systems. Chris Roberts was apparently able to overwrite code on the airplane’s Thrust Management Computer while aboard a flight, causing a plane to move laterally in the air.”
Roberts denies having done this during a real flight and Boeing has claimed in-flight entertainment systems are isolated from flight and navigation systems. However, when it comes to the aviation industry the stakes are even higher with regards to potential flaws in IoT systems. “As airlines transition to even more advanced systems leveraging these technologies more attention needs to be focused on underlying system weaknesses that could represent a security and safety risk,” Garlati explains. He asks:
What are airports doing well on this front and what's still missing?
What is the one major step all airports should take to avert an attack (perhaps hiring a cyber expert? employ a crisis management system?)
“Airport managers must understand that security is likely to fail if it’s not built in by design,” Garlati says. “In fact, I would go so far as to say that if it’s not secure, it doesn’t work. So the mindset of pen testing and bringing on cyber security experts at a later date to ‘fix holes’ is a false economy- having said that, it is obviously better than nothing,” he adds. “But industry as a whole needs to change this mindset and work towards building and developing systems and devices with security at the core. The march of silicon means that it is becoming more powerful and so it is possible to add traditional security layers embedded at the hardware level, making it resilient to attack.”
Hackers with physical access will be able to accomplish significantly more damage, and traditionally access is the difficult part. “In the case of Chris Roberts hacking an aircraft physical access was the easy part, using the seat electronic box (SEB) which was present for the inflight entertainment system,” Pore says. “Network segmentation would definitely have slowed down the attack and perhaps prevented Roberts from accessing critical aircraft management systems. It was noted in the FBI interview that Roberts used default credentials to gain access. There is always significant risk involved with leaving physical access available and not changing default credential sets.”
10. Retail Stores and Databases
Last year, Tripwire announced the results of a study conducted by Atomic Research that found that retail security lags behind that of many other sectors.
While many of the cybersecurity risks facing retailers aren’t strictly IoT related, a growing number of them are. For instance, in 2014, hackers managed to break into Target’s financial systems unit by way of an HVAC unit. The criminals responsible for the attack managed to steal network credentials from an HVAC vendor who had worked at a number of Target facilities in addition to other large retailers.
Retail environments, like critical sectors, need to go undergo a paradigm shift in network security.
Retail companies remain one of the most attractive targets for hackers because they store vast troves of financial data. Retail-related IoT devices will only add to that volume.
“Retail environments, like critical sectors, need to go undergo a paradigm shift in network security,” Pore says. “If organizations are only deploying perimeter focused tools to keep threats out, they will likely become the next victim. In addition to traditional technologies such as firewalls, IDS, IPS, and anti-virus, the shift to protecting core assets using analytics needs to be implemented. This can be accomplished using network behavior coupled with indicator correlation to detect threats and undesired behavior. Watching, profiling, and alarming on threshold of critical assets such as point-of-sale machines reaching out to the internet will help organizations from becoming the next headline.”
About the Author
You May Also Like






